The digital security landscape is evolving rapidly in 2025. Businesses face increasingly sophisticated cyber threats.
Machine learning has become the cornerstone of modern cybersecurity solutions. This guide explores the latest cybersecurity trends for business protection.
Organizations must adapt their security protocols to stay ahead of threat actors. Understanding these trends builds robust cyber resilience.
Advanced Threat Detection: Next-Generation Security Solutions
Modern threat detection represents the future of proactive cybersecurity solutions. Systems analyze millions of data points in real-time.
These platforms use machine learning algorithms to recognize patterns. The technology processes network traffic and user behavior simultaneously.
Security analytics can detect zero-day exploits within minutes. Traditional methods are no longer sufficient against evolving malicious attacks.
Companies implementing automated security monitoring report 65% faster threat identification. The systems continuously learn from new threat intelligence.
READ THIS BLOG : 26 Best Tools for Small Business 2025 – Grow Revenue 10x Faster
Machine Learning in Cybersecurity: Preventing Advanced Persistent Threats
Machine learning transforms how organizations combat sophisticated cyber threats. Advanced algorithms analyze network behavior to identify anomalous activities.
These systems excel at detecting advanced persistent threats that remain hidden for extended periods. Predictive analytics help security teams anticipate attack vectors.

The technology examines historical attack patterns to forecast future security breaches. This proactive approach reduces vulnerability windows significantly.
Behavioral analysis creates baseline profiles for normal user activities. Any deviation triggers immediate investigation for potential insider threats.
Modern Security Risks: Protecting Against Advanced Cyberattacks
Modern cybersecurity faces both opportunities and challenges. Threat actors increasingly use advanced tools to create sophisticated attacks.
These malicious attacks are harder to detect using conventional security protocols. Organizations must implement advanced defense mechanisms to counter emerging threats.
Security teams need specialized training to recognize sophisticated attacks. The threat landscape evolves as cybercriminals leverage new tools.
Businesses must invest in next-generation security solutions that differentiate between legitimate and malicious content effectively.
Cloud Security Automation: Advanced Protection for Multi-Cloud Environments
Cloud security automation addresses the complexity of protecting distributed business environments. Advanced tools provide unified security monitoring across platforms.
This approach eliminates blind spots that threat actors often exploit in hybrid infrastructure setups. Automated vulnerability management continuously scans cloud resources.
Machine learning algorithms prioritize vulnerabilities based on potential business impact. This intelligent risk assessment helps security teams focus effectively.
Infrastructure security ensures consistent protection policies across all cloud deployments. Automated compliance checking maintains robust cyber defense postures.
Zero Trust Architecture: Implementing Enhanced Identity Verification
Zero Trust Architecture represents a fundamental shift in network security philosophy. Enhanced identity verification ensures thorough authentication for every access request.
This approach assumes that cyber threats can originate from anywhere. Continuous authentication uses behavioral biometrics and machine learning to verify identities.
The system monitors keystroke patterns and application usage behaviors. Any suspicious activity triggers immediate re-authentication or access revocation.
Context-aware access controls consider multiple factors when granting permissions. This intelligent approach reduces security breach risks significantly.
Quantum-Resistant Encryption: Preparing for Post-Quantum Cybersecurity
Quantum computing poses unprecedented challenges to traditional encryption methods. Organizations must transition to quantum-resistant encryption proactively.
This approach protects sensitive data protection investments for the future. Post-quantum cryptography uses mathematical problems quantum computers cannot solve.

The National Institute of Standards and Technology has standardized several quantum-resistant algorithms. Early adoption gives businesses competitive advantages.
Cryptographic agility allows organizations to update encryption methods without major overhauls. This flexibility is crucial as quantum computing advances.
Governance and Compliance: Meeting 2025 Data Protection Requirements
Security governance frameworks ensure responsible use of technology in cybersecurity solutions. New regulations require transparency in decision-making processes.
Organizations must document how systems process and protect sensitive information. Compliance automation helps businesses meet evolving data protection requirements.
Automated tools continuously monitor regulatory changes and adjust security protocols accordingly. This proactive approach reduces compliance risks.
Ethical practices build trust with customers and stakeholders. Organizations must implement bias detection and fairness measures.
Behavioral Analytics: Using Technology to Detect Insider Threats and Anomalies
Behavioral analytics revolutionizes insider threat detection through advanced machine learning techniques. These systems establish baseline behaviors for users.
Insider threats often exhibit gradual behavioral changes that traditional security measures cannot detect. User behavior analysis examines access patterns and data usage.
Sudden changes in patterns may indicate compromised accounts or malicious insiders. The technology provides early warning signals before security breaches.
Anomaly detection algorithms continuously adapt to changing organizational dynamics. They distinguish between legitimate changes and suspicious activities.
Automated Incident Response: How Technology Reduces Cyber Attack Recovery Time?
Automated incident response dramatically reduces time between threat detection and containment. Modern systems execute predefined response procedures within seconds.
This rapid response capability minimizes damage and reduces recovery costs. Orchestrated security workflows coordinate multiple security tools for comprehensive response.
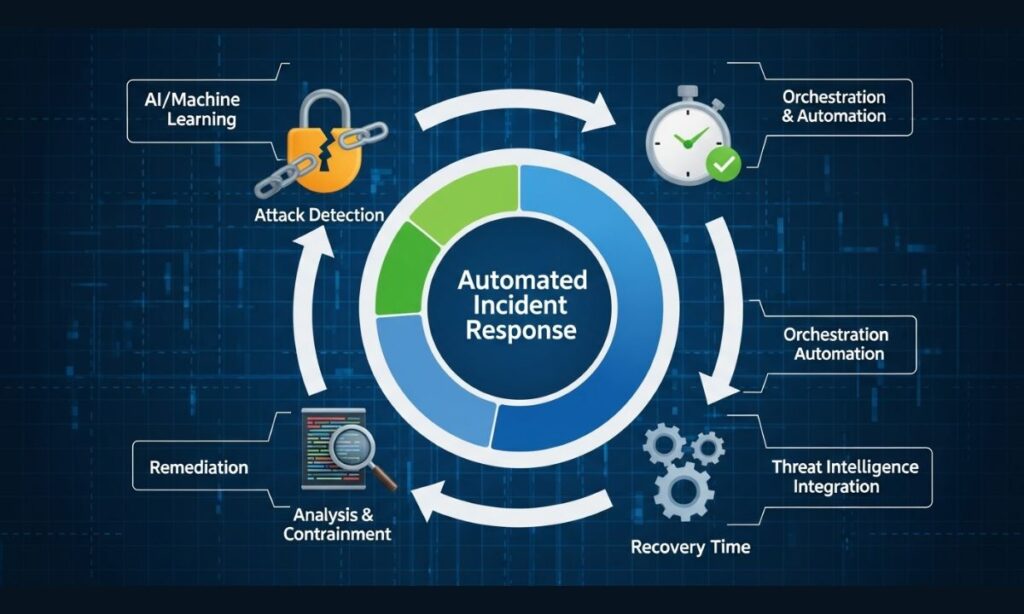
Automation handles routine tasks while escalating complex issues to human analysts. This hybrid approach optimizes both speed and accuracy.
Self-healing systems can automatically remediate certain types of cyber attacks without human intervention. This ensures consistent response quality.
READ THIS BLOG : Top 10 Cybersecurity Priorities for Small Businesses 2025
Privacy-Preserving Technology: Securing Sensitive Data in Machine Learning Systems
Privacy-preserving technology protects sensitive information while enabling advanced security analytics. Federated learning allows organizations to benefit from collective threat intelligence.
This approach maintains data protection while improving overall cyber defense capabilities. Homomorphic encryption enables computation on encrypted data.
This technology allows security systems to analyze sensitive information while maintaining confidentiality. Organizations can leverage powerful analytics while meeting requirements.
Differential privacy adds mathematical noise to datasets to prevent individual identification. This enables security research while protecting personal information.
Frequently Asked Question
What are the main benefits of advanced threat detection in 2025?
Advanced threat detection provides real-time analysis of data points, detecting sophisticated attacks within minutes and reducing false positives.
How does machine learning improve cybersecurity for businesses?
Machine learning analyzes patterns to predict and prevent threats, creating adaptive security systems that learn from new attack methods.
What are the biggest security risks organizations face?
Primary risks include sophisticated phishing attacks, advanced social engineering, and complex malware created using modern tools.
Why is Zero Trust Architecture important for modern businesses?
Zero Trust assumes all access requests are potentially malicious, using continuous authentication to verify every user interaction.
How can businesses prepare for quantum computing threats?
Organizations should implement quantum-resistant encryption algorithms and develop flexibility to quickly adapt to post-quantum security requirements.
Conclusion
The cybersecurity trends of 2025 represent a fundamental transformation in digital security. Machine learning, behavioral analytics, and automated incident response provide unprecedented protection.
Businesses must embrace these technologies to maintain effective cyber resilience. Success requires strategic planning and gradual implementation.
Organizations should prioritize threat intelligence, vulnerability management, and security monitoring enhancements. Investment in advanced cybersecurity solutions determines future effectiveness.

David is a seasoned SEO expert with a passion for content writing, keyword research, and web development. He combines technical expertise with creative strategies to deliver exceptional digital solutions.







